Based on a recent article in Wired Magazine, I thought it might be helpful to touch on the “dark web” a bit. After all, I do teach CMWEB 270 (Web Application Security) and often talk about the dark alleys on the Internet. But, first, a few disclaimers. Seriously. I do not condone nor support the illegal use of computer resources in any manner. Laws exist for a reason. I am providing this information for educational purposes only. Should you choose to use anything in this post for malicious purposes, I will be glad to testify against you in court. I hope this is sufficiently clear to everyone reading this. That being said, you should know a little about it (without risking exposure to malicious sites and there are a lot of them). Keep in mind the current estimate is that the deep web (including the dark web) is 550 times larger than the visible web. This is the content not indexed by standard search engines.
So, let’s learn a little about the dark web. First, many sites will appear to have a top level domain of .onion. [This link takes you to a Wikipedia article about this “domain.”] Dot onion is a [not so] subtle reference to TOR (The Onion Router). You need to be part of the TOR network in order to access these resources. These are not valid top level domains. They are 16 letter and number hashes (numbers from 2 – 7) representing an 80 bit number in base 32. In theory, you can replace any .onion address with .tor2web.org and still visit the site (of course, you won’t have as much anonymity).
Next, in order to access these resources, you need a browser which can connect to the TOR network. Surprisingly, there is a variant of Firefox which does just that. This is the browser available from the TOR Project. You can download and install the browser. No, I am not providing a direct link to the download. I chose to do this on a removable USB drive (yes, you can run this as [sort of] a portable app) and leave little trace on the computer itself. For those responsible for corporate networks, what I just said should be very scary.
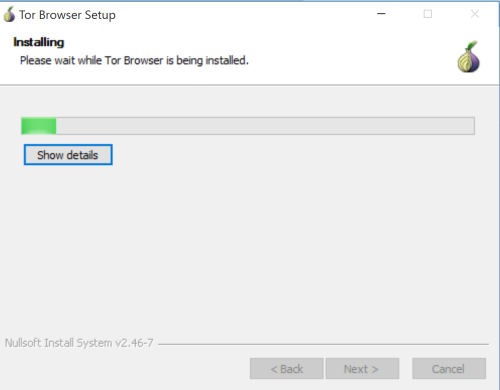
Here is what the screen looks like when you install the software.
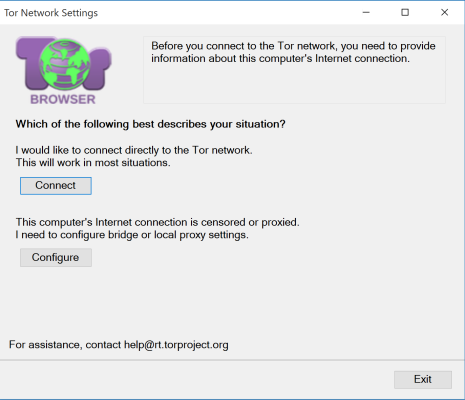
Once installed, you need to connect to the TOR network.
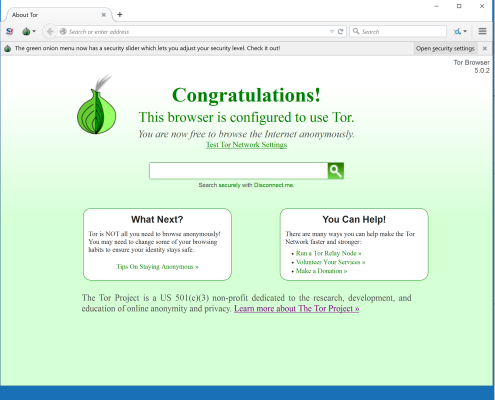
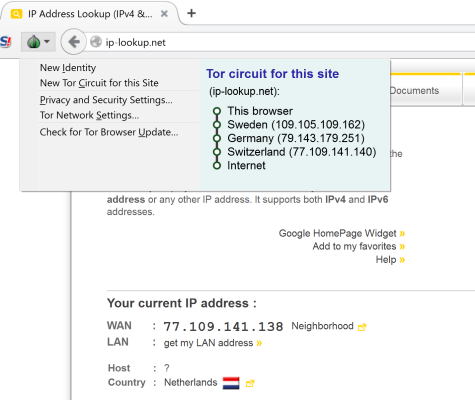
If successful, you see a screen like this.
You can configure your “location” and change it at will. In this case, you see that I made a quick trip to the Netherlands one afternoon (I was also in Germany and a few other countries).
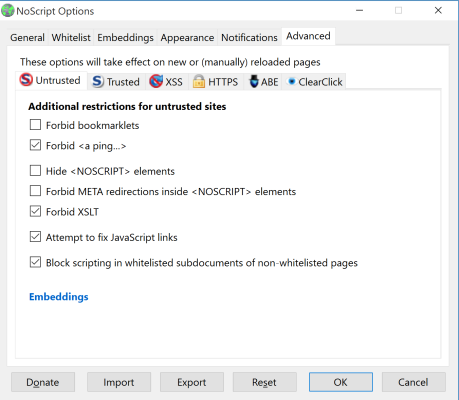
This tool lets you brows in a fairly anonymous way. There are also NoScript settings you may wish to employ to disable JavaScript – a notorious means of tracking via cookies (and so much more). By default, the NoScript plugin is enabled with some basic settings.
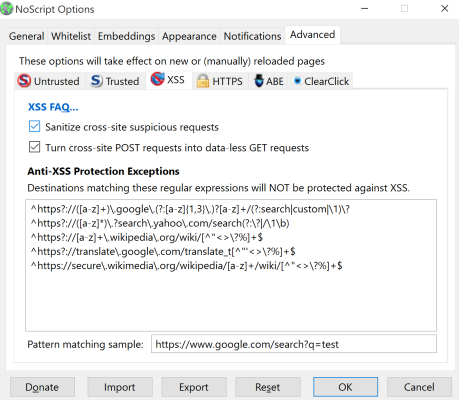
There are also defenses against XSS (Cross Site Scripting) and ABE (Application Boundaries Enforcer) can be enabled.
Ok, Mark, I get it. Let’s see some of these famous sites. First, The search engine Duck Duck Go (famous for enforcing anonymity) has a presence. Note the address ends in .onion. You can always click on these images to see a larger view.
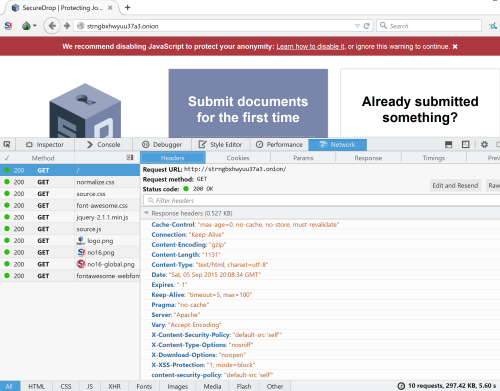
For whistle blowers, there are a number of sites (such as the New Yorker [Secure Drop] – below).
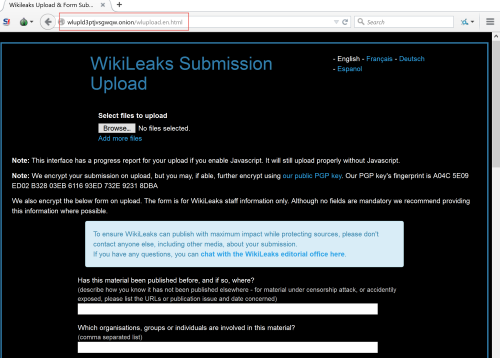
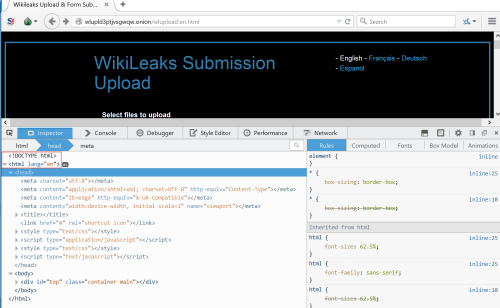
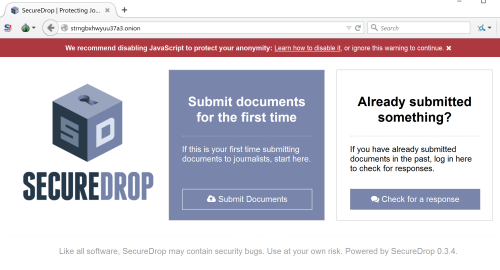 Let’s not forget about WikiLeaks either.
Let’s not forget about WikiLeaks either.
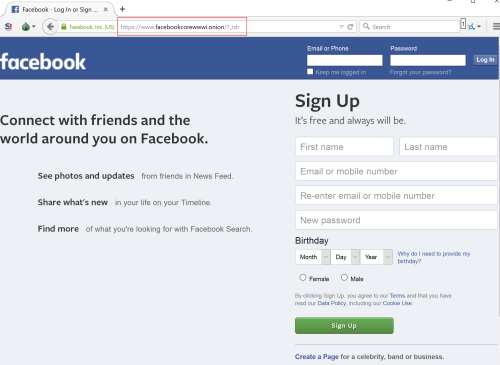
Amazingly, even Facebook has a presence. Anonymity <-> Facebook. Yeah, I don’t get it either. You will note that Facebook even went so far as to create an almost human readable address. Personally, I don’t think I would feel comfortable signing up for a Facebook account on the dark web. Just my paranoia, I guess.
Amazingly, almost all these sites are HTML5 and take advantage of relatively recent coding best practices.
You can even view headers using the TOR browser just as you would in Firefox. Of course, they appear to come form the .onion top level domain.
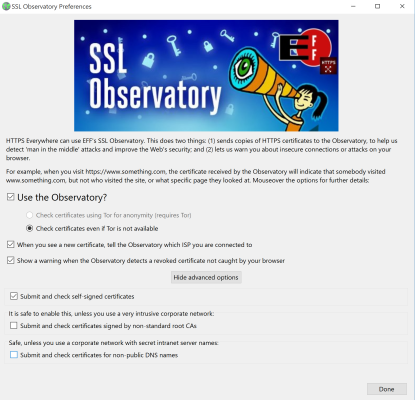
For those who wish to be even more cautious, there is the capability to activate the EFF (Electronic Frontier Foundation) SSL Observatory.
Ok, you now have a little clearer understanding of what lies in the dark web. It is just much larger than what we typically see and allows for much greater anonymity. Sadly, much of this has been taken over by those with nefarious purposes. However, the technology itself is neither good nor evil. It is just how it is used. Hence my opening remarks about not using any computer resource for illegal activities.
I am curious if you found this quick overview helpful. As always, I look forward to your comments.



Great overview, Mark! I have never understood the dark web, or taken the time to research it. I am surprised at how little effort it takes to get to it. To be that “anonymous” on the web, you would think it would take a little more than one file download and change of IP. Not something I want to explore!
It is rather scary, isn’t it?