The CMWEB 270 class I teach covers many of the fundamentals of ethical hacking. Of course, one of the main problems one encounters when teaching ethical hacking is providing links to vulnerable websites. Yes, one can easily create a vulnerable site. However, many hosting providers don’t like you to post the vulnerable sites on their servers (for example, in a reseller account, it is possible to walk across multiple “sites” depending on the vulnerability being exploited). Wouldn’t it be nice if there was the ability to spin up a vulnerable sandbox, cover the exploits, and then remove the sandbox. This is precisely what the Hack.Me is all about. This service is provided by eLearnSecurity and is free for academic use (you must agree to abide by their terms of service).
I thought it might be helpful to review some of the fundamentals of working with this environment. Obviously, you first need an account. Once you have an account, you can create your own environments or you can use one of the provided examples. If you are just getting started, I recommend trying out some of the pre-built modules (search through the examples). For example, there is a U-Hack-It! example (complete with tutorials). You spin up a sandbox (which you have a unique URL to access). You can then try out various exploits. A simple example would be to supply a username of hacker’ OR ‘a’=’a and a password of haha’ OR 1+2=’3 to take advantage of a common SQL injection vulnerability. The results are shown in the screen capture below.
Once you have mastered the fundamentals, consider trying out some of the other examples. Since I have spent a fair amount of time covering WordPress vulnerabilities in the past, I thought it might be time to focus a bit on Joomla!. Let’s try out the supplied example using Joomla! 1.5 and reset our password. Yes, it really is as simple as shown below. This sort of information is readily available via search engines. If you are running Joomla! 1.5, this might be a wake up call to upgrade your system. Note: I am certainly not advocating an attack on any vulnerable installation. In fact, such an attack is highly illegal and you will likey be prosecuted. However, from an ethical hacking perspective, you should be aware of these sorts of vulnerabilities (after all, hackers certainly are aware). Google (and other search engines make this sort of information readily available).
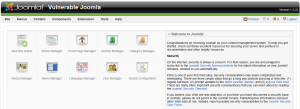
Once you spin up the Joomla sandbox, you will see a screen like the following:
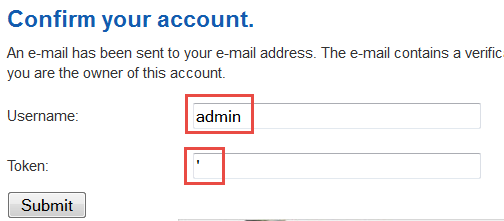
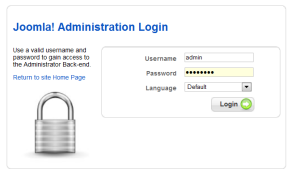
One of the exploits in this version of Joomla is to trick the system into thinking you have reset your password (of course, you use the default login of admin). Simply append the following string to your Joomla! 1.5 installation initial page – /index.php?option=com_user&view=reset&layout=confirm. Yep, that is all you need to do to break Joomla! 1.5. The software thinks that you have just sent a valid password reset and that it has sent you an email to confirm. That emila contains a verification token. Joomla! next asks you to enter the token. In my case, I chose to enter a single tick mark instead.
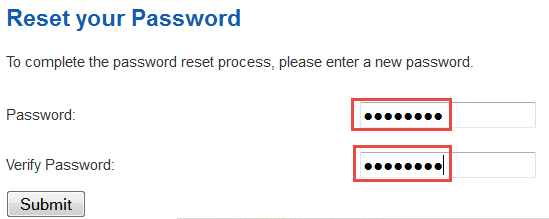
You will immediately be asked to change your password. In my case, I chose that old standby of mine in my classes – fredderf.
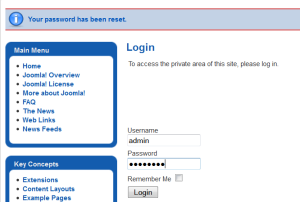
And… I receive confirmation that my password has been reset. As you can see, I could login to the site at this point.
However, why not try out the back end. I did just change the admin password after all. So I go to the administration part of the site and enter the credentials I just modified.
And I am now in the site as the administrator. Yes, it really was that simple. Again, if you are reading this and have a Joomla! 1.5 site, upgrade now. Don’t wait. At a minimum, get rid of the admin user. Then upgrade. Don’t put it off. Who knows who else is reading this post.
Ok, now you have an idea of how to use Hack.me and work with supplied examples. But, what if you want to populate your own? You can also do that.
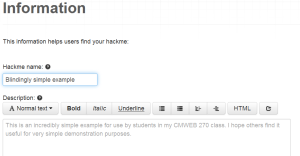
For example, I created a blindingly simple example which I discussed at the Web Professionals and Adobe User Group meeting last night.
Surprisingly, this even showed up on the main list of examples for the site (perhaps it was a slow day when I modified this). I know it is for the latest HackMes, but it managed to stay there for a while.
First, you should create your working example locally and then make a zip archive of all files. Obviously, this will be more complicated if you want to use databases.
You next create your HackMe and provide basic information.
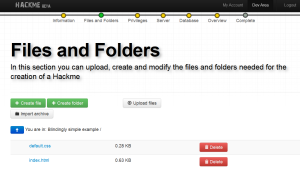
You then upload necessary files and folders (I find it easiest to upload a zip archive, but you can upload individual files).
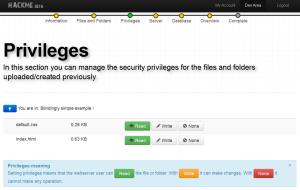
You next set the privileges for these files and folders.
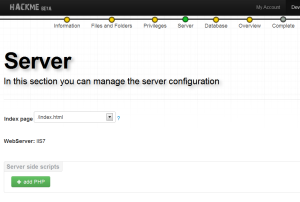
You then specify the server environment. In my case, I chose IIS 7.
Next, if you are using databases, you define those and populate them. In my case, I did not take this approach (after all, it is a blindingly simple example).
Of course, you then test your work, save it and publish it. The final stap indicates whether others can view your work or not.
Even after you have published your work, someone will need to review it (this is a hosted facility, after all). If you want to try out the blindingly simple example, just visit it. You should be prompted to spin up a new sandbox (which is 99% yours).
After you agree to the terms of service, you can use the sandbox. I recommend deleting the sandbox when you are finished (no need to take up a lot of extra space on the server if you are not using it).
I am curious as to your thoughts regarding Hack.Me. Do you plan to use it? I look forward to your comments.




Hello Mark,
Thank you for a great post on the basics of Hackme.
I was hoping you could answer one simple question. I can’t seem to find an answer anywhere.
Once you Sandbox is created, can you attack the URL itself?
Could I for example run a whois or DNS look up against it and try to access the Server ?
Thanks for any answer or advise.
I am looking for some network I can legally attack.
Cyber
As far as I know, what you ask is not possible. I believe these are dynamic and only exist for a short time. I also don’t think the terms and conditions of HackMe allow for this sort of attack. Perhaps it would be best to contact the site itself?
Best always,
Mark