During this summer (2013), I taught a course on content management systems in various cities across the US. I focused on WordPress, Joomla! and Drupal. In San Francisco, Sam Bowne (@sambowne) participated in the class and focused on security aspects of these applications. He reported that he was able to quickly reveal the password hash contents for WordPress. Joomla! took a bit longer. Drupal was the most secure. Sam also included his notes about this on his site. Since many readers may not be that familiar with the tools employed (or recognize the potential exposure), I thought it best to expand on the process.First you need a WordPress site. I chose to install one locally using Windows Server 2008 R2 and IIS. Obviously, there are many ways to install a WordPress site. I am running this environment on my MacBook and plan to use this for demonstration purposes at our August WebProfessionals and Adobe User Group meeting. A screen capture is shown below. [You can always click on these images to enlarge them to full size].
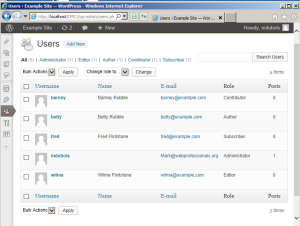
Once you authenticate to WordPress, you can create additional users. This is what I have done below. Note – this is the first point of potential exposure – if you are using WordPress on a remote server, it is a REALLY good idea to access your login via https instead of http. The former means that your credentials will be encrypted and not visible as plain text. The latter means you are sending plain text for both your username and password. This means if you are using a wifi network, anyone can intercept the traffic and read those credentials. Tools like Wireshark are readily available and relatively easy to use to obtain the plain text.
Ok, I added a few users to the site (see below).
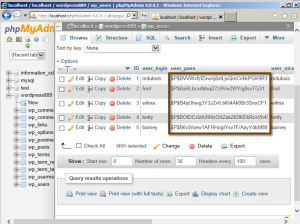
Each user of the application has a different password. These are stored as hash values in the WordPress database. I can examine the contents of the database using tools like PHPMyAdmin (yes, I had to install this in IIS; I suspect most readers are more familiar with this than MS SQL Server). The contents of the table are shown below. I have placed a box around the actual values. They look pretty secure, don’t they?
So why is this a problem? It is securely placed in a database. One would need to hack in to the entire site to obtain this, wouldn’t they? First, I know many instances where individuals routinely send their backup files via email to themselves (or post them in a Dropbox account or other online service). This means it is often easier to get to the actual password hashes than one would think. Ok, but these are still pretty secure aren’t they? Keep in mind, if I can see them, I can copy them and store them in a text file for later processing.
This is where we need to be aware of tools like HashCat. There is also a GUI version. Tools like this are designed to crack such password hashes. Yes, there are legitimate reasons why one may need to recover a password (which is why these tools exist). Consider seized computers (from criminals) or websites which are used for illicit activities. Most of these sorts of tools rely on “dictionaries” of possible passwords (or take a brute force approach).
Some dictionaries I have found useful include:
- Wordlists – download the English big wordlist as a start.
- Dictionaries – you can find a number of different languages
- RockYou – most of the commonly used passwords will be found in this list
HashCat is a command line program. You need to tell it the type of hash one is working with. For WordPress, you specify a switch of -m 400 (note there is a space between m and 400). You also need to specify the file containing hash values and the dictionary you plan to use.
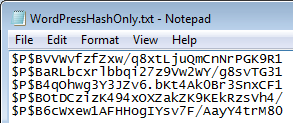
If you refer to the PHPMyAdmin screen above, one would need to extract the individual hash values and store them in a text file. I have done so and display this as an image below.
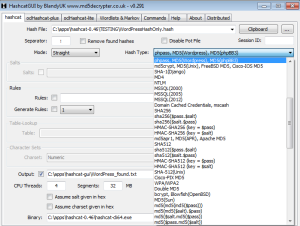
I prefer using the GUI as I don’t need to recall all the switch choices. Of course, when running HashCat at the command line, one can always specify a switch of -h to view the help information. Here is a screen capture showing the possible hash choices. Note that I have already specified WordPress (hey, it is pretty popular).
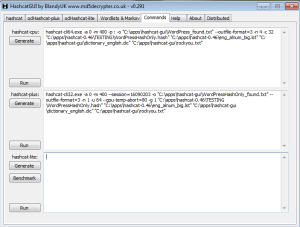
I also like that one can generate necessary commands in the GUI (for those who want to learn more about the choices when using the command shell. Note that I have included a couple of examples in the screen capture below.
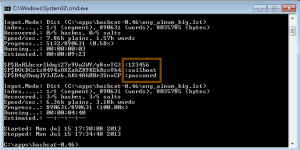
The result is to run the program. In this case, you see the results for 3 of the 5 passwords. Yes, the remaining 2 are more complex, but they could eventually be cracked as well.
If you have a larger series of hashes, you can always direct the output to a text file for later analysis.
My point behind this post is to alert you to the fact that password hashes can be readily cracked. The longer your password, the more complex it is will help reduce the chances that your password will be readily cracked. I also strongly encourage every reader to use a different password on each site. There are a number of password vault technologies which one can use to help in this matter.
I look forward to your comments. Please note that I must approve these first as this site has been subject to a number of spam messages over time (I filter most automatically, but a few still manage to sneak through so I must manually approve all).